SSL Certificate
Internet security is essential and one of the cornerstones of security is SSL certificates. Let's get familiar with them.
Table of Contents
- What is an SSL Certificate?
- How does SSL/TLS communication work?
- Why use an SSL certificate?
- Validation of SSL certificates
- Types of SSL Certificates
- Certificate Authorities
What is an SSL Certificate?
An SSL certificate is essentially a digital certificate for a domain. SSL stands for Secure Socket Layer (Wiki about SSL/TLS), a protocol created by company Netscape in 1994 during the "internet prehistory" (for example, Google was founded in 1998). It was created to establish secure and encrypted communication over the internet between a user's browser and a web server. The certificate is issued by a trusted third party, known as a certificate authority (CA), which verifies the certificate applicant/web server owner and issues a "confirmation." Today, the successor to the SSL protocol, the standardized TLS protocol (Transport Layer Security), is used, but the original name for SSL certificates remains commonly used.
Secure communication and the use of an SSL certificate were previously identified in the browser's address bar by the presence of "https://" before the domain name, where the letter "S" stands for Secure (HTTPS - Hypertext Transfer Protocol Secure), and the padlock symbol. Nowadays, the use of SSL certificates is completely standard, and browsers, on the other hand, display warnings about insecure sites.
What is HTTPS?
HTTPS is a method of encrypting data (information) transmitted between the browser and the web server. Encryption protects website visitors and users from eavesdropping and man-in-the-middle attacks, where a hacker can steal information sent to a website, such as credit card details or login credentials. An attacker can also inject malicious content or perform other harmful attacks. Securing communication with the HTTPS protocol is now the standard for all websites.
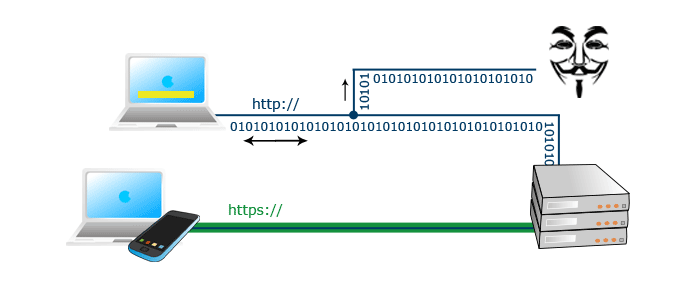
How does SSL/TLS Communication Work?
To set up secure HTTPS communication, a process called a handshake occurs between the browser and the server, where information about how communication will proceed (cipher types, encryption keys, etc.) is exchanged. The SSL certificate is used at the beginning of the communication, where asymmetric encryption is used to exchange keys and verify the server. Here, the trustworthiness of the certificate authority that issues the SSL certificate and confirms the authenticity of the owner is very important. If everything is in order, HTTPS communication is established, and data security proceeds using symmetric encryption (encryption and decryption using a single key).
You can view the step-by-step TLS 1.3 connection process between a client and a server on the excellent page Illustrated TLS Connection - Every byte explained and reproduced.
Asymmetric encryption works with a pair of encryption keys – public and private (Wiki - Asymmetric cryptography). The public key can be made public, and if anyone encrypts a message with this key, only the owner of the corresponding private key can decrypt it. The same applies in reverse, which is used for authentication – a message encrypted with the private key can only be decrypted with the corresponding public key. If we know the public key belongs to a particular entity (verified by a trusted authority), we also know with whom we are communicating.
Why Use an SSL Certificate?
An SSL certificate is necessary to create and ensure secure HTTPS communication on the internet. There are many reasons to use an SSL certificate. But beware! An SSL certificate does not protect websites from hackers. If you don't update applications like WordPress or a programmer poorly codes the website, an SSL certificate will not protect the site from being compromised.
By deploying an SSL certificate and securing HTTPS communication, we primarily protect users, site visitors from eavesdropping on communication, from injecting malicious code into the site, or from altering the content (inserting ads, modifying content). This is the main reason to deploy an SSL certificate even on the smallest one-page website, where we think there is nothing to protect.
A key reason for deploying an SSL certificate is login forms and other forms on websites where sensitive data is entered, which must be protected during transmission over the internet from eavesdropping, theft, and misuse.
Websites without an SSL certificate are negatively labeled "NOT SECURE" in web browsers, which appears very untrustworthy.
New technologies can only be used in browsers with secured communication. New protocols HTTP/2+3 significantly speed up website loading, and without HTTPS, they do not support all features.
SSL certificates ensure compliance with legal regulations and standards regarding privacy protection and adherence to standards.
Advantages of HTTPS Communication
- Secure communication between the user's browser and server
- Protection of sensitive information
- Use of new technologies (fast HTTP/2 protocol, new CSS properties)
- Authentication of the counterpart (web server)
- SEO benefits for pages in Google search
- Removal of the "Not Secure" label on the website
Disadvantages of HTTPS Communication
- Need to obtain an SSL certificate
- The SSL certificate must be renewed regularly
- Technical setup of HTTPS communication
- Potential website functionality issues
Validation of SSL certificates
For a trusted SSL certificate to be issued, the certificate authority (CA) first performs verification. This process can only be carried out by the owner or operator of a specific domain, ensuring that the certificate is granted only to an authorized party. There are three levels of verification that define the types of SSL certificates.
Domain Validation Certificates (DV SSL)
To obtain a certificate, it is sufficient to verify the domain, which is the fastest, simplest, and automated method of verification. The certificate authority verifies only the legitimacy of access to the domain specified in the certificate request. Verification takes place by sending an e-mail to one of the five domain mailboxes: admin@, administrator@, webmaster@, hostmaster@, or postmaster@. These emails are given by the verification rules and cannot be changed. Alternatively, verification can be done by placing a generated file into the domain's FTP space or by setting a specific DNS record.
You can view the step-by-step process of domain validation on the page How domain verification works (DV certificates).
Organization Validation Certificates (OV SSL)
Unlike domain validation, this is a manual process where the certificate authority must verify the actual existence of the applicant. The domain is verified as with DV certificates, and the existence of the business is also confirmed. Data is retrieved from public authoritative databases, and each CA has its own verification procedures.
The advantage of organization certificates is the ability to authenticate and confirm the legitimacy of the communication, meaning that the site I am visiting belongs to the company I expect.
Extended Validation Certificates (EV SSL)
EV SSL certificates are the most trusted SSL certificates. In the past, the company's name was displayed directly in the green address bar next to the domain. This changed in 2019, and now organization certificates are a better choice offering the same properties at a lower cost.
Types of SSL Certificates
Through gradual development, several types of SSL certificates were created, differing mainly in the number of secure domains. The types themselves then also offer different verification methods.
Single Domain SSL Certificate
SSL certificates for a single domain are the most commonly ordered. These certificates secure a specific internet domain. They can secure business, personal websites, or any kind of project. Single domain SSL certificates are issued by certificate authorities for use on both www and non-www versions of the address. For securing a single domain, the cheapest SSL certificates from our offer are also suitable.
WildCard SSL Certificate
WildCard certificates, a.k.a. star certificates, offer a unique feature: the ability to secure an unlimited number of subdomains under your main domain. They save server administrators significant time and costs in installation and management. In the request for a WildCard certificate, you specify an asterisk (*) before the domain (e.g., *.domainxyz.com), which allows you to secure any subdomain at the specified level.
Multi-Domain SSL Certificate
Multi-domain SSL certificates allow you to secure multiple different domains with a single SSL certificate. These certificates can secure dozens of domains simultaneously, even with different TLDs (.COM, .EU, .DE, .ES etc.), distinguishing them from WildCard SSL certificates that secure an unlimited number of subdomains.
The use of a multi-domain SSL certificate offers simpler certificate management and often a more favorable price for the security of one domain. They are ideal for businesses requiring simultaneous security multiple domains from different TLDs. Multi-domain SSL certificates are also suitable for securing Microsoft Exchange.
Certificate Authorities
The certificate authority verifies the certificate request and issues the certificate. There are many certificate authorities around the world, but for a CA to be trusted, it must meet certain standards. These are defined by operating system manufacturers (Microsoft, Apple) or directly by browser makers, such as Mozilla for its Firefox browser, which has its own Mozilla CA Certificate Program and maintains its list of trusted authorities.
Certificate authorities are members of the CA/Browser Forum. Members include not only CAs but also browser manufacturers, operating system developers, and other IT companies (list of members). This forum plays a crucial role in the development and regulation of certification services, with its own rules and requirements for certificate issuance that certificate authorities must follow.
SSL certificates on the SSLmentor project
On our website, you will find high-quality and trusted SSL certificates from selected certificate authorities.
What's Next?
Back to Help
Found an error or don't understand something? Write us!






